Either as fundamental part of the corporate strategy, or even driven by compliance mandates, all organizations are coming up with a plan and specific measures to protect their most valuable assets. Nowadays, we have realized that data are the crown jewels that should be protected and be kept secure. Data include everything from intellectual property, patterns, personal data, competitive or financial information. But also, data are everywhere, in corporate premises, cloud applications or mobile devices, making it harder to protect them than before.
And, what about the most common information security principle that says “You can’t protect what you can’t see.”? There are many uses cases where organizations don’t know what data they own, why they collected them, where they are located, who has access to them etc.
So how can you be sure for the data you possess and protect them accordingly?
We can help you identify the corporate or personal data (for GDPR compliance) that exist anywhere in your corporate environment, in file servers, content management repositories, databases or workstations, by offering you world class data discovery and classification solutions.
Data protection solutions offered by Performance Technologies enable complete data protection, PCI scope reduction and enablement of secure analytics, with format-preserving encryption, tokenization, and stateless, on-demand key management for securing data as it is captured, processed, and stored across databases, applications, data warehouses, Big Data and cloud environments.
What is data-centric protection?
It’s the ability to provide end-to-end protection for data in-use, in-motion and at-rest. Voltage SecureData protects data independent of the subsystems that use it. It protects sensitive data as soon as it is acquired and helps ensure that it is used, transferred, and stored in protected form. Selected applications decrypt the data at the time that it is processed, while others work with encrypted or masked data.
Voltage SecureData with Hyper FPE “de-identifies” sensitive personally identifiable information (PII) such as social security numbers (SSN), and other high value data, rendering it useless to attackers in the event of a security breach. This allows companies to securely leverage the de-identified data for big-data analytics, and collaborate with shared data between other agencies, contractors or companies.
Voltage SecureData neutralizes data breaches by making your protected data absolutely worthless to an attacker, whether it is in production, analytic systems, or test/development systems, such as training and quality assurance.
Voltage can help:
Identity and access management is disconnected from security management in many IT organizations. Traditionally, identity and access management has focused on getting business users the right access to do their jobs, regardless of complexity from cloud and mobile apps, while security teams have focused on defending the organization from external and internal threats.
But both want the same thing – to protect sensitive information from misuse or theft using a method that is transparent and convenient for users. And both teams have capabilities that would be useful for the other.
Identity and Access Management solutions offered by Performance Technologies provide an intelligent identity framework that leverages your existing IT assets and new computing models like Software as a Service (SaaS) by reducing cost and ensuring compliance across physical, virtual, and cloud environments. With Identity Manager solutions, you can make sure that your business has the most current user identity information. You can retain control at the enterprise level by managing, provisioning, and deprovisioning identities within the firewall and extending to the cloud. Through streamlined user administration and processes, Identity Manager helps organizations reduce management costs, increase productivity and security, and comply with government regulations.
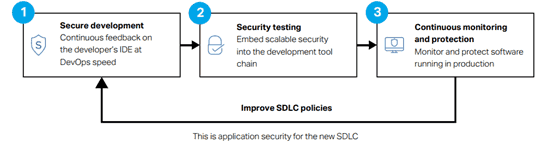
While the statistics are staggering, application security awareness is increasing. But this also comes at a time when there is tremendous pressure on developers to build new, better applications – faster than ever before. As a result, development teams are turning to more agile processes and DevOps to further streamline workflows and reduce time-to-market. This is also forcing companies to consider a new approach to the software development lifecycle (SDLC) – a new SDLC that looks holistically at the software development process and integrates security testing from beginning to end.
Fortify – the undisputed leader in application security – provides reliable, comprehensive security through all stages of the new SDLC. It delivers a flexible, comprehensive suite of application security technologies that target businesses wanting to integrate agile techniques with greater protection and control. Together, these technologies focus on three distinct areas of protection: secure development, security testing, and continuous monitoring and protection.
Fortify is the only application security provider to offer static application
security testing (SAST), dynamic application security testing (DAST), interactive application security testing (IAST), and runtime application self-protection (RASP) on premise and on demand. Because Fortify Software Security Center and Fortify on Demand are fully compatible, you can choose the solution that’s right for your business.
General Data Protection Regulation (GDPR) (1) by the European Parliament and the Council, was adopted on April 2016 and focuses on the protection of natural persons, with regards to the processing of personal data and on the free movement of such data.
It came to replace the Data Protection Directive 95/46/EC and was designed to harmonize data privacy laws across Europe, to protect and empower all EU citizens data privacy and to reshape the way organizations across the region approach data privacy.
Any handling of Personal Data throughout its entire
life cycle, from collection to deletion, is considered “processing”. Even remote access is considered “processing.”
“Personal data” is defined in GDPR as any information relating to a person who can be identified, directly or indirectly, in particular by reference to an identifier such as a name, an identification number, location data, online identifier or to one or more factors specific to the physical, physiological, genetic, mental, economic, cultural or social identity of that person.
| Main Requirements of the Regulation | The GDPR introduces the following rights for data subjects: |
|
|
GDPR went into effect on 25 May 2018 and has international reach. So, from that time on, any organization that processes data of EU data subjects encounters new, uniform data protection requirements or strict fines for non-compliance, 4% of annual turnover or €20 million per incident, whichever is higher.
(1) EU GDPR regulation 2016/679 published document
Although GDPR isn’t actually a totally different approach on data protection, organizations must be compliant with it from 25 May 2018 and onwards. To that end, organizations must review their existing data protection framework, business processes and security systems to understand the gaps with GDPR mandates, and take legal, business or technical measures to achieve and maintain compliance and thus avoid fines.
Performance Technologies is here to assist you in fast, effective and full compliance with GDPR regulation, throughout the entire data lifecycle, from sensitive data discovery to implementation and monitoring of your data protection and compliance strategy.
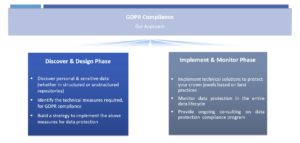
Though our partnership with leading industry vendors, we are providing solutions that best cover each organization’s needs to comply with the regulation. Some of the solutions we offer for GDPR compliance are among the following areas:
Ask us for more information!
☎ +30 210 99 47 100
☞ Evrymedontos 4, Athens GR10435, GREECE, Registration Number:123782001000
This ebook offers insights and considerations, and outlines how the IBM Security Guardium data protection platform can help.